Q. who developed the concept of semaphore ?
a) Dekker
b) Tanenbaum
c) Dijkstra
d) Kruskal
Q.Which among the following is a boot loader?
a) LILO
b)MBR
c)FAT
d)POST
Q.Which among the following is a clipping algorithm
a)Kruskal's
b)Dijkstra's
c)Cohen-Sutherland
d)Prim's
A specially designed blog for sharing and distributing UGC NET Computer Science examination materials viz Exam Syllabi, Previous Questions,Current Trends, Topics like Mobile Computing, Operating System, Database Management System,Computer Networks,System analysis and Design, and Programming using C & C++ etc.
Search Topics....
Monday, August 29, 2011
Sunday, August 28, 2011
Time Complexity Factor Big O of Sorting Algorithms
Sorting algorithms used in computer science are often classified by:
Computational complexity (worst, average and best behaviour) of element comparisons in terms of the size of the list (n). For typical sorting algorithms good behavior is O(nlogn) and bad behavior is  . Ideal behavior for a sort is
. Ideal behavior for a sort is 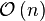 , but this is not possible in the average case.Comparison-based sorting algorithms, which evaluate the elements of the list via an abstract key comparison operation, need at least
, but this is not possible in the average case.Comparison-based sorting algorithms, which evaluate the elements of the list via an abstract key comparison operation, need at least  comparisons for most inputs.
comparisons for most inputs.
 . Ideal behavior for a sort is
. Ideal behavior for a sort is 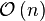 , but this is not possible in the average case.Comparison-based sorting algorithms, which evaluate the elements of the list via an abstract key comparison operation, need at least
, but this is not possible in the average case.Comparison-based sorting algorithms, which evaluate the elements of the list via an abstract key comparison operation, need at least  comparisons for most inputs.
comparisons for most inputs.Computational complexity of swaps (for "in place" algorithms).
Memory usage (and use of other computer resources). In particular, some sorting algorithms are "in place". This means that they need only  or
or 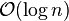 memory beyond the items being sorted and they don't need to create auxiliary locations for data to be temporarily stored, as in other sorting algorithms.
memory beyond the items being sorted and they don't need to create auxiliary locations for data to be temporarily stored, as in other sorting algorithms.
 or
or 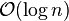 memory beyond the items being sorted and they don't need to create auxiliary locations for data to be temporarily stored, as in other sorting algorithms.
memory beyond the items being sorted and they don't need to create auxiliary locations for data to be temporarily stored, as in other sorting algorithms.Recursion. Some algorithms are either recursive or non-recursive, while others may be both (e.g., merge sort).
Stability: stable sorting algorithms maintain the relative order of records with equal keys (i.e., values). See below for more information.
Whether or not they are a comparison sort. A comparison sort examines the data only by comparing two elements with a comparison operator.
General method: insertion, exchange, selection, merging, etc.. Exchange sorts include bubble sort and quicksort. Selection sorts include shaker sort and heapsort.
Adaptability: Whether or not the pre sortedness of the input affects the running time. Algorithms that take this into account are known to be adaptive.
Courtesy : Wikipedia
Questions on C Programming
Q.1 Literal means
(A) a string.
(B) a string constant.
(C) a character.
(D) an alphabet.
Q.2 Choose the correct answer
(A) Casting refers to implicit type conversion.
(B) Coercion refers to implicit type conversion.
(C) Casting means coercion.
(D) Coercion refers to explicit type conversion.
Q.3 printf (“%d”, printf (“tim”));
(A) results in a syntax error
(B) outputs tim3
(C) outputs garbage
(D) outputs tim and terminates abruptly
Q.4 Output of the following program fragment is
x = 5;
y = x++;
printf(“%d%d”, x, y);
(A) 5, 6
(B) 5, 5
(C) 6, 5
(D) 6, 6
Q.5 The value of an automatic variable that is declared but not initialised will be
(A) 0
(B) -1
(C) unpredictable
(D) none of these
Q.7 The following program fragment
int *a;
*a = 7;
(A) assigns 7 to a
(A) a string.
(B) a string constant.
(C) a character.
(D) an alphabet.
Q.2 Choose the correct answer
(A) Casting refers to implicit type conversion.
(B) Coercion refers to implicit type conversion.
(C) Casting means coercion.
(D) Coercion refers to explicit type conversion.
Q.3 printf (“%d”, printf (“tim”));
(A) results in a syntax error
(B) outputs tim3
(C) outputs garbage
(D) outputs tim and terminates abruptly
Q.4 Output of the following program fragment is
x = 5;
y = x++;
printf(“%d%d”, x, y);
(A) 5, 6
(B) 5, 5
(C) 6, 5
(D) 6, 6
Q.5 The value of an automatic variable that is declared but not initialised will be
(A) 0
(B) -1
(C) unpredictable
(D) none of these
Q.7 The following program fragment
int *a;
*a = 7;
(A) assigns 7 to a
(B) results in compilation error
(C) assigns address of a as 7
(C) assigns address of a as 7
(D) segmentation fault
Q.8 A pointer variable can be
(A) passed to a function as argument.
(B) changed within function.
(C) returned by a function.
(D) assigned an integer value.
Q.9 ‘C’ is often called a
(A) Object oriented language
Q.8 A pointer variable can be
(A) passed to a function as argument.
(B) changed within function.
(C) returned by a function.
(D) assigned an integer value.
Q.9 ‘C’ is often called a
(A) Object oriented language
(B) High level language
(C) Assembly language
(C) Assembly language
(D) Machine level language
Q.10 The loop in which the statements within the loop are executed at least once is called
(A) do-while
Q.10 The loop in which the statements within the loop are executed at least once is called
(A) do-while
(B) while
(C) for
(C) for
(D) goto
Q.11 The control automatically passes to the first statement after the loop in
(A) continue statement
Q.11 The control automatically passes to the first statement after the loop in
(A) continue statement
(B) break statement
(C) switch statement
(C) switch statement
Bank Exams: IBPS conducts Written Exam for Clerical Cadre like...
Bank Exams: IBPS conducts Written Exam for Clerical Cadre like...: IBPS, an autonomous body, has been authorised by the IBA and has received mandates from 19 Public Sector Banks to conduct the recruitment ...
Saturday, August 27, 2011
Exam Tips for HSST CS / CA
Give importance to the following areas
- port number of FTP , HTTP , etc..
- Time complexity of Search and sort..
- TCP / IP
- OSI Reference Model
- Search engines like google, page rank etc..
- if possible go through the summary pages of OS , Networks, Communication
- Go through the IT Quiz published in computer magazines
- Refer source books for Plus two courses
- previous questions of UGC and GATE
- Never attend the question 100% dubious
Remember that Last time the cut off marks for HSST computer science exam was only 35
Friday, August 26, 2011
Questions from Plus Two Syllabi
What is hypertext?
How static webpage differs from dynamic webpage?
Which html tag is called anchor tag?
What is an applet?
How would you round off a value from 1.66 to 2.0?
Why java is called platform independent?
How static webpage differs from dynamic webpage?
Which html tag is called anchor tag?
What is an applet?
How would you round off a value from 1.66 to 2.0?
Why java is called platform independent?
XML stands for________________
What is a byte code?
What is JIT?
FTP stands for ________________
What is a normalized relation?
What is a byte code?
What is JIT?
FTP stands for ________________
What is a normalized relation?
PERL stands for _______________
What is Lynx?
SRC is the attribute of _________ tag.
In DHTML , D means_______
Write html code to display A2+B2 = C4 in a webpage.
Name the protocol used to create email links
What will happen if in a C program you assign a value to an array element whose subscript exceeds the size of array?
Name the extension of VB Project files
By changing ______property, we can control the resizing behavior of form
What is a tuple?
Name the window in VB which contains names of files used in a project
What is cardinality?
What is cardinality?
option control in VB is also called _______
What is degree of a relation ?
BR tag is a ________ type of html tag.What is degree of a relation ?
What is DML and DDL?
Name the software used for viewing webpages.
What is encryption?
What is encryption?
_______is the event of Timer Control
Wednesday, August 24, 2011
Mobile Operating systems
A mobile operating system, is a a mobile platform, or a handheld operating system, is the operating system that controls a mobile device or information appliance—similar in principle to an operating system such as Windows, Mac OS X, or Linux that controls a desktop computer or laptop. However, they are currently somewhat simpler, and deal more with the wireless versions of broadband and local connectivity, mobile multimedia formats, and different input methods.
Android
Android is a mobile operating system for mobile devices such as mobile phones and tablet computers developed by the Open Handset Alliance led by Google.Android consists of a kernel based on the Linux kernel, with middleware, libraries and APIs written in C and application software running on an application framework which includes Java-compatible libraries based on Apache Harmony.Android uses the Dalvik virtual machine withjust-in-time compilation to run compiled Java code. ( Source :wikipedia )
Some other mobile operating systems are Symbian , iOS , BlackBerry OS , Windows CE etc.
More >>
Monday, August 22, 2011
Terms associated with Web Technology
What is a favicon ?
Favicons : Favourites icons are tiny logos that appear at the far left of a browser’s address bar. They can be static or animated, depending on your browser, and give websites that use them a little extra personality.
What is https?
Hypertext Transfer Protocol Secure (HTTPS) is a combination of the Hypertext TransferProtocol (HTTP) with SSL/TLS protocol.
What is LYNX?
Lynx is one of the most popular web browsers for command-line interfaces.
Lynx is one of the most popular web browsers for command-line interfaces.
SEO: Search Engine Optimization is a technique which helps search engines find and rank your site higher than the millions of other sites in response to a search query.
What is captcha?
A CAPTCHA or Captcha is a type of challenge-response test used in computing to ensure that the response is not generated by a computer.
A CAPTCHA or Captcha is a type of challenge-response test used in computing to ensure that the response is not generated by a computer.
What is Trap Door?
Trap doors, also referred to as backdoors, are bits of code embedded in programs by the programmer(s) to quickly gain access at a later time, often during the testing or debugging phase. If an unscrupulous programmer purposely leaves this code in or simply forgets to remove it, a potential security hole is introduced. Hackers often plant a backdoor on previously compromised systems to gain later access. Trap doors can be almost impossible to remove in a reliable manner. Often, reformatting the system is the only sure way.
Sunday, August 21, 2011
RankMaker Version 3.0 Ready For Download
Hi all...
You can download RankMaker Version 3.0 from today..Once again thanks for using RankMaker software for your exam preparation and giving your valuable suggestion by participating the on-line poll.
Friday, August 19, 2011
Poll Four Result : Floppy Disk Invented by IBM
Sony | 7 (16%) |
Logitech | 3 (7%) |
Creative | 4 (9%) |
IBM | 28 (66%) |
Thursday, August 18, 2011
RankMaker 3.0 Beta Test
Currently we are designing the next version of RankMaker , a software found to be very effective in preparing various exams. Nearly 5000 persons downloaded this software from this blog. This time we are very keen to hear from you about what all the facilities likely to have in next version. Based on some feedback received from the users we are employing an online survey given in the right side of this Blog. Please spare five minutes to take the survey and inform us your important suggestions.
If any body wants to tell us more you can drop a mail to psctrainer@ymail.com
if you are not familiar with RankMaker you can Download RankMaker Ver2.0
Best Wishes
PSCTrainer Team
Wednesday, August 17, 2011
What is Deadlock in Operating System ?
Deadlocks
In a multiprogramming environment, several processes may compete for a finite no.of resources. A process requests resources, if the resources are not available at that time, the process enters a wait state. it my happen that waiting process will never again change state, because the resources have requested are held up by other waiting processes. this situation is called Deadlock.
A deadlock state occurs when two or more processes are waiting indefinitely for an event that can be caused only by one of the waiting process.
A Deadlock situation may occur if and if four necessary conditions hold simultaneously in the system. namely mutual exclusion, hold and wait, no preemption and circular wait.
Prevention of Deadlock.
To prevent deadlock we ensure that at lease of the necessary condition (namely mutual exclusion, hold and wait, no preemption and circular wait ) never holds.
Deadlock Avoidance
Deadlock avoidance is less stringent than the prevention algorithm is to have priori information on how each process will be utilizing the resources.
Banker’s Algorithm
It is a Deadlock avoidance algorithm . This algorithm needs to know the maximum no.of each resource class that may be requested by each process.
PHP stands for Hypertext Preprocessor
Q? : _______ is a powder used in laser printers to form the images on a paper [ computer gk ]
Answer: toner
Q? : Worms and Trojan Horses are examples of : [ computer gk ]
Answer: malware
Q? : Who invented the Computer [ PSC Computer GK ]
Answer: BABBAGE
Q? : Which of the following is first generation of computer :
Answer: EDSAC
Q? : Which command lists files in MS-DOS ? [ Computer , Quiz ]
Answer: dir
Q? : What is the internet TLD of France [ Computer GK Internet ]]
Answer: .fr
Q? : What is the capacity of a standard PC floppy ? [ Computer , Quiz ]
Answer: 1.44 MB
Q? : What does PHP stands for [ Computer Abbreviation HSST GK ]
Answer: Hypertext Preprocessor
Q? : What does Google means [ Computer GK ]
Answer: 1 followed by 100 zeros
Q? : What does FTP stands for ? [ Computer Abbreviation HSST GK ]
Answer: File Transfer Protocol
Q? : What does ADSL stands for ? [ Computer Abbreviation HSST GK ]
Answer: Asymmetric Digital Subscriber Line
Q? : URL stands for : [ Computer Quiz ]
Answer: Uniform Resource Locator
Q? : The utility which can be used to clean the windows registry is: [ Computer GK ]
Answer: Regedit
Q? : The utility which can be used to clean the windows registry is : [ computer gk ]
Answer: regedit
Q? : The TTL field is inside the ____ header [ computer gk ]
Answer: IP
Q? : The port number used by the HTTP protocol is [ Computer GK ]
Answer: 80
Q? : The port number used by the HTTP protocol is : [ computer gk ]
Answer: 80
Q? : The port number used by SMTP is : [ computer gk ]
Answer: 25
Q? : The name Andy Bechtolsheim associated with [ Computer GK ]
Answer: Google
Q? : The Laser printer was invented at : [ computer gk ]
Answer: Xerox
Search More From PSCTrainer
Tuesday, August 16, 2011
PSC Notification Vocational Instructor in Computer Science
Gazzette Date: 29-07-11
Last Date: 31-08-11
Category No: 212/2011
Applications with a latest passport size photograph uploaded are invited online only from qualified candidates for appointment in the under mentioned post in Kerala Government services.
1 Department : Kerala Vocational Higher Secondary Education.
2 Name of Post : Vocational Instructor in Computer Science.
3 Scale of pay : ` 14620 – 25280/-
4 No. of vacancies : 1 (One)
More Details at keralapsc.org
What is PageRank Algorithm ?
PageRank Algorithm is the algorithm employed by Google Search Engine to optimize its search result page. PageRank is a link analysis algorithm, named after Larry Page and used by the Google Internet search engine, that assigns a numerical weighting to each element of a hyperlinked set of documents, such as theWorld Wide Web, with the purpose of "measuring" its relative importance within the set.
Q. The Page Rank algorith is used by : [ From PSC HSST Question Paper 2004 ]
a) www.google.com
b) www.yahoo.com
c) www.altavista.com
d) www.go.com
Saturday, August 13, 2011
Operating System Notes based on the Text book by Silberschatz and Galvin
Kernel : One program running at all times on the computer.
TAT ( Turn Around Time ) : The delay between job submission and job completion.
Spooling : Simultaneous peripheral operations online . It allows the CPU to overlap the input of one job with the computation and output of other jobs.
Batch System : Allows automatic job sequencing by a resident operating system thus improves over all utilization of the computer.
Multiprogramming : Several jobs are kept in memory at one time, the CPU is switched back and forth among them to increase CPU utilization and decrease the total needed execution time.
Time Shared OS : Allows many users to use a computer system interactively at the same time.
Parallel System : More than one CPU in close communication, it share the computer bus, some times share memory and peripheral devices. it has increased throughput and reliability.
Distributed System: Collection of processors that don't share memory or a clock. It provides the user with access to the various resources located at remote site.
Time Shared OS : Allows many users to use a computer system interactively at the same time.
Parallel System : More than one CPU in close communication, it share the computer bus, some times share memory and peripheral devices. it has increased throughput and reliability.
Distributed System: Collection of processors that don't share memory or a clock. It provides the user with access to the various resources located at remote site.
Real Time System : It is used when there are rigid time requirements on the operation of a processor or the flow of data.
Hard Real Time System : Well defined, fixed time constraints. Used as control device in a dedicated application.
Soft Real Time System : Less stringent timing constraints and don't support dead line scheduling.
More Notes>>
Father of Computer Science is Alan Turing
Poll Three Result Announced : Answer : Alan Turing
Alan Turing | 20 (31%) |
Tim Bernesli | 2 (3%) |
John Vohn Neuman | 3 (4%) |
Charles Babbage | 38 (60%) |
Note : 63 persons participated in the poll and only 20 made write answer..Its shameful. Thanks for participating the poll.
Participate in Next Poll
Best Wishes
PSCTrainer
Download Your HSST Computer Science Exam Hall Ticket Now
Hall ticket download for HSST Computer Science Examination available from official website Kerala PSC. Note down the following for downloading the hall ticket.
Category Code : District/Statewide : Barcode No. : :Date of Birth
if you have forgotten the Barcode you can use below format to get the same .
To know Barcode KPSC BC CategoryCode To 537252(from the mobile no. which was given in the application of the Category)
Category Code : District/Statewide : Barcode No. : :Date of Birth
if you have forgotten the Barcode you can use below format to get the same .
To know Barcode KPSC BC CategoryCode To 537252(from the mobile no. which was given in the application of the Category)
Best Wishes
www.psctrainer.com
Friday, August 12, 2011
Port Number : PSC Sure Question
In every PSC examinations, the question about PORT number is repeating.. so go through some important port numbers.
Telnet (Remote Login) : Port number is 23
FTP (File Transfer Protocol) : Port number is 21
HTTP (Hypertext Transfer Protocol) : Port number is 80
RPC (Remote Procedure Calls) : Port number is 135
SMTP (Simple Mail Transfer) : Port number is 25
POP3 (Post Office Protocol ) : Port number is 110
IMAP (Internet Message Access) : Port number is 143
Thursday, August 11, 2011
Poll Two Result Announced : Answer : Facebook
Mark Zukerberg is associated with?
Orkut
2 (4%)
Facebook
40 (88%)
Youtube
1 (2%)
Yahoo
2 (4%)
Note : 45 persons participated in the poll and 40 made write answer..Thanks for participating the poll.
Participate in Next Poll
Best Wishes
PSCTrainer
Orkut
2 (4%)
40 (88%)
Youtube
1 (2%)
Yahoo
2 (4%)
Note : 45 persons participated in the poll and 40 made write answer..Thanks for participating the poll.
Participate in Next Poll
Best Wishes
PSCTrainer
Tuesday, August 9, 2011
PSC Question 101/2008 : Solved
1. _______ is a powder used in laser printers to form the images on a paper
a) cartridge
b) ribbon
c) gel
d) toner
2. Worms and Trojan Horses are examples of :
a) hardware
b) firmware
c) malware
d) freeware
3. _______ printers work by selectively heating regions of special heat sensitive paper
a) impact
b) inkjet
c) thermal
d) dot-matrix
4. The ISI mark is given by
a) BIS
b) ISO
c) ANSI
d) IEEE
5.The Laser printer was invented at :
a) Canon
b) Epson
c) HP
d) Xerox
6. In 100BASE-T, " T " stands for :
a) type
b) traffic
c) twisted pair
d) bytes
7. Which among the following utilities can detect a bad sector?
a) CHKDSK
b) SCANDISK
c) Both A & B
d) None
8. The port number used by SMTP is :
a) 13
b) 21
c) 25
d) 27
9. A packet filter is a type of :
a) compiler
b) firewall
c) inverter
d) search tool
10. The TTL field is inside the ____ header
a) Ethernet
b) IP
c) TCP
d) HTTP
11. GRUB is a / an :
a) Search Tool
b) Editor
c) Boot Loader
d) Compiler
12. Power-on-self-test is built into the
a) BIOS
b) Hard disk
c) SMPS
d) UPS
13. Powerpoint can embed content from other applications through :
a) NFS
b) OLE
c) JDBC
d) CUPS
14. In Powerpoint presentations, individual pages are called :
a) Cells
b) Tables
c) Columns
d) Slides
15. The port number used by the HTTP protocol is :
a) 13
b) 25
c) 80
d) 255
16. The utility which can be used to clean the windows registry is :
a) chkdsk
b) scandisk
c) regedit
d) fixboot
17. Indiscriminate sending of unsolicited bulk messages is known as :
a) instant messaging
b) flaming
c) phishing
d) spamming
18. Kerberos is a _________ protocol
a) Network authentication
b) Data compression
c) Network Management
d) File Transfer
19. Athlon series of processors are made by :
a) AMD
b) Intel
c) IBM
d) Motorola
20. The ability to replace components of a computer , while it is operating is called
a) De-fragmentation
b) Hot swapping
c) Boot Strapping
d) OLE
Answer are given in blue color . if any errors found, pls comment
More >>
a) cartridge
b) ribbon
c) gel
d) toner
2. Worms and Trojan Horses are examples of :
a) hardware
b) firmware
c) malware
d) freeware
3. _______ printers work by selectively heating regions of special heat sensitive paper
a) impact
b) inkjet
c) thermal
d) dot-matrix
4. The ISI mark is given by
a) BIS
b) ISO
c) ANSI
d) IEEE
5.The Laser printer was invented at :
a) Canon
b) Epson
c) HP
d) Xerox
6. In 100BASE-T, " T " stands for :
a) type
b) traffic
c) twisted pair
d) bytes
7. Which among the following utilities can detect a bad sector?
a) CHKDSK
b) SCANDISK
c) Both A & B
d) None
8. The port number used by SMTP is :
a) 13
b) 21
c) 25
d) 27
9. A packet filter is a type of :
a) compiler
b) firewall
c) inverter
d) search tool
10. The TTL field is inside the ____ header
a) Ethernet
b) IP
c) TCP
d) HTTP
11. GRUB is a / an :
a) Search Tool
b) Editor
c) Boot Loader
d) Compiler
12. Power-on-self-test is built into the
a) BIOS
b) Hard disk
c) SMPS
d) UPS
13. Powerpoint can embed content from other applications through :
a) NFS
b) OLE
c) JDBC
d) CUPS
14. In Powerpoint presentations, individual pages are called :
a) Cells
b) Tables
c) Columns
d) Slides
15. The port number used by the HTTP protocol is :
a) 13
b) 25
c) 80
d) 255
16. The utility which can be used to clean the windows registry is :
a) chkdsk
b) scandisk
c) regedit
d) fixboot
17. Indiscriminate sending of unsolicited bulk messages is known as :
a) instant messaging
b) flaming
c) phishing
d) spamming
18. Kerberos is a _________ protocol
a) Network authentication
b) Data compression
c) Network Management
d) File Transfer
19. Athlon series of processors are made by :
a) AMD
b) Intel
c) IBM
d) Motorola
20. The ability to replace components of a computer , while it is operating is called
a) De-fragmentation
b) Hot swapping
c) Boot Strapping
d) OLE
Answer are given in blue color . if any errors found, pls comment
More >>
Monday, August 8, 2011
Poll One Result Announced : Answer : James Gosling
Man behind JAVA programming Langauge ?
Richard St. Barbe Baker
0 (0%)
Richard Stalman
3 (6%)
47 (94%)
Mark Elliot Zuckerberg
0 (0%)
Note : 50 persons participated in the poll and 47 made write answer..It was the question asked in last HSST Computer Science Exam.
Best Wishes
PSCTrainer
Saturday, August 6, 2011
System Software & Compiler Construction
Q. What is a System software ?
System software is computer software designed to operate the computer hardware and to provide a platform for running application software. eg: Operating SystemQ. What is an assembler ?
Assembler converts each assembly language statement into the corresponding machine-language statement.
There are two types of assemblers.
One-pass assemblers go through the source code once and assume that all symbols will be defined before any instruction that references them.
Two-pass assemblers create a table with all symbols and their values in the first pass, then use the table in a second pass to generate code.
Q.What are various steps to design an assembler?
1. Statement of problem:
2. Data structure:
3. Format of data bases:
Here we specify the format and content of each of the data bases task that must be undertaken even before describing the specific algorithm underlying the assembly design.
4 Algorithm: There are two passes in this
Q.Define Lexical Analysis
lexical analysis is the process of converting a sequence of characters into a sequence of tokens. A program or function which performs lexical analysis is called a lexical analyzer.
Q.What are various steps to design an assembler?
1. Statement of problem:
2. Data structure:
3. Format of data bases:
Here we specify the format and content of each of the data bases task that must be undertaken even before describing the specific algorithm underlying the assembly design.
4 Algorithm: There are two passes in this
Q.Define Lexical Analysis
lexical analysis is the process of converting a sequence of characters into a sequence of tokens. A program or function which performs lexical analysis is called a lexical analyzer.
Q.What is YACC ?
YAAC is a computer program used as a parser generator developed by Stephen C. Johnson at AT&T for the Unix operating system. The name is an acronym for "Yet Another Compiler Compiler." It generates a parser (the part of a compiler that tries to make syntactic sense of the source code) based on an analytic grammar written in a notation similar to BNF.
More>>
More>>
Thursday, August 4, 2011
Good News for HSST CS/CA Exam Aspirants.
Kerala Govt sanctioned about 300 more Computer Science / Computer Application Plus Two batches. It s good news for those who applied for HSST exam . Within two or three years, there is a chance of appointment in these vacancies...
In this blog we are publishing various computer science topics..There is a chance of typographical and some other type of errors in the questions as well as answers.. if you come across any such errors please inform us at the email id psctrainer@ymail.com
Best Wishes
PSCTrainer Team
Wednesday, August 3, 2011
Artificial Intelligence
Q. What is A. I ?
The theory and development of computer systems able to perform tasks that normally require human intelligence, such as visual perception, speech recognition, decision-making, and translation between languages.
Q.What is the term used for describing the judgmental or commonsense part of problem solving?
A. Heuristic
B. Critical
C. Value based
D. Analytical
E. None of the above
Q.What stage of the manufacturing process has been described as "the mapping of function onto form"?
A. Design
B. Distribution
C. project management
D. field service
E. None of the above
B. Critical
C. Value based
D. Analytical
E. None of the above
Q.What was originally called the "imitation game" ? A. LISP B. The Logic Theorist C. The Turing Test D. Cybernetics |
A. Design
B. Distribution
C. project management
D. field service
E. None of the above
Q.Decision support programs are designed to help managers make:A. budget projections B. visual presentations C. business decisions D. vacation schedules
|
Tuesday, August 2, 2011
PSC Mock Exam @ www.psctrainer.com
You can take mock exam for various PSC Examinations @ PSCTrainer MockExam Centre.
Monday, August 1, 2011
Important Notes on Software Engineering
Q. Define Software Engineering
The establishment and use of sound engineering principles in order to obtain economically software that is reliable and works efficiently on real machines.
Q. Differentiate Software engineering methods, tools and procedures.
Methods: Broad array of tasks like project planning, cost estimation etc..
Tools: Automated or semi automated support for methods.
Procedures : Holds the methods and tools together. It enables the timely development of
computer software.
Q. Write the disadvantages of classic life cycle model.
Disadvantages of classic life cycle model :
(i) Real projects rarely follow sequential flow. Iteration always occurs and creates problem.
(ii) Difficult for the customer to state all requirements
(iii) Working version of the program is not available. So the customer must have patience.
Q. What do you mean by task set in spiral Model?
Each of the regions in the spiral model is populated by a set of work tasks called a task set that are adopted to the characteristics of the project to be undertaken.
Q. What is the main objective of Win-Win Spiral Model?
The customer and the developer enter into the process of negotiation where the customer may be asked to balance functionality ,performance and other product against cost and time to market.
Q. Which of the software engineering paradigms would be most effective? Why?
Incremental / Spiral model will be most effective.
Reasons:
(i) It combines linear sequential model with iterative nature of prototyping
(ii) Focuses on delivery of product at each increment
(iii)Can be planned to manage technical risks.
Q. Write the objective of project planning ?
It is to provide a framework that enables the manager to make reasonable estimates of resources, cost and schedule.
Q. Write a short note on 4GT.
Fourth Generation Technique. 4GT encompasses a broad array of software tools. Each tool enables the software developer to specify some characteristics of software at a higher level.
Q. What is LOC ? How it is used for project estimation?
LOC : Lines of Code. It is used as estimation variable to size each element of the software. It requires considerable level of detail..
Q. Write the formula to calculate the effort in persons-months used in Dynamic multi variable Model?
Software Equation :E=[LOC * B0.333/P]3 *(1/t4) Where E is effort in person-months, t is project duration, B is special skills factor, P is productivity parameter.
Q. What are the two project scheduling methods ?
PERT- Program Evaluation and Review Techniques
CPM- Critical Path Method
Q. What is RMMM?
Risk Mitigation, Monitoring and Management Plan. It is also called Risk Aversion.
Q. List the tools or methods available for rapid prototyping.
Rapid prototyping (Speed)
(i) 4GT
(ii) Resuable software components
(iii) Formal specification and prototyping environments.
Q. What is the need for modularity ?
Need for modularity: Easier to solve a complex problem. Can achieve reusability. Best effort and complexity reduces.
Q. What is Software Architecture?
The overall structure of the software and the ways in which that software provides conceptual integrity for the system.
Q. What are the models are used for Architectural design?
Structural models
Framework models
Dynamic models
Process models
Functional models
Q. What is cohesion?
It is a measure of the relative functional strength of a module. (Binding)
Q. What is Coupling?
Measure of the relative interdependence among modules.
(Measure of interconnection among modules in a software structure.)
Q. Define Stamp coupling.
When a portion of the data structure is passed via the module interface , then it called stamp coupling.
Q. Define common coupling.
When a number of modules reference a global data area, then the coupling is called common coupling.
Q. What is Real Time Systems.
It provides specified amount of computation with in fixed time intervals. RTS sense and control external devices, respond to external events and share processing time between tasks.
Q.Define Distributed system .
It consists of a collection of nearly autonomous processors that communicate to achieve a coherent computing system.
Q. What are the contents of HIPO diagrams?
Visual table of contents, set of overview diagrams, set of detail diagrams.
Q. What are the aspects of software reuse.
Software development with reuse
Software development for reuse
Generator based reuse
Application system reuse
Q. What is CASE ?
CASE : Computer Aided Software Engineering
CASE provides the engineer with the ability to automate manual activities and to improve engineering
insight.
Q. Define CASE Tools.
CASE Tools :
• Computer Aided Software Engineering
• It is a System software
• Provide Automated support for software process activities
• Includes program used to support software process activities
• Such as Requirement Analysis, System Modeling, Debugging and Testing
Q. How do we define Software Quality?
Software Quality :
• Conformance to explicitly stated functional and performance requirements, explicitly documented
development standards
• Implicit characteristics, expected for professional developed software
Q. What are the Factors of Software Quality?
Factors of Software Quality :
• Portability
• Usability
• Reusability
• Correctness
Subscribe to:
Comments (Atom)